Hello,
Today, I’ve developed a solution for the CrowdStrike issue that has caused significant outages for numerous major companies using PowerShell WPF and SCCM. Microsoft recently released a recovery tool specifically designed to address this problem; however, it requires USB devices for recovery operations.
Supplying, imaging, and distributing large numbers of USB devices to various locations can be hard and time-consuming. Fortunately, with SCCM and your existing network infrastructure, you can deploy the recovery solution via PXE.
Note:
I developed this script with the help of ChatGPT. While I have tested it numerous times, use it at your own risk.
Step 1: Download the CrowdStrike Recovery Tool
To download the tool, visit the GitHub repository using the link below: https://github.com/gokhanyildan/CrowdStrikeRecoveryTool
Step 2: Create an SCCM Task Sequence and Deploy the Tool
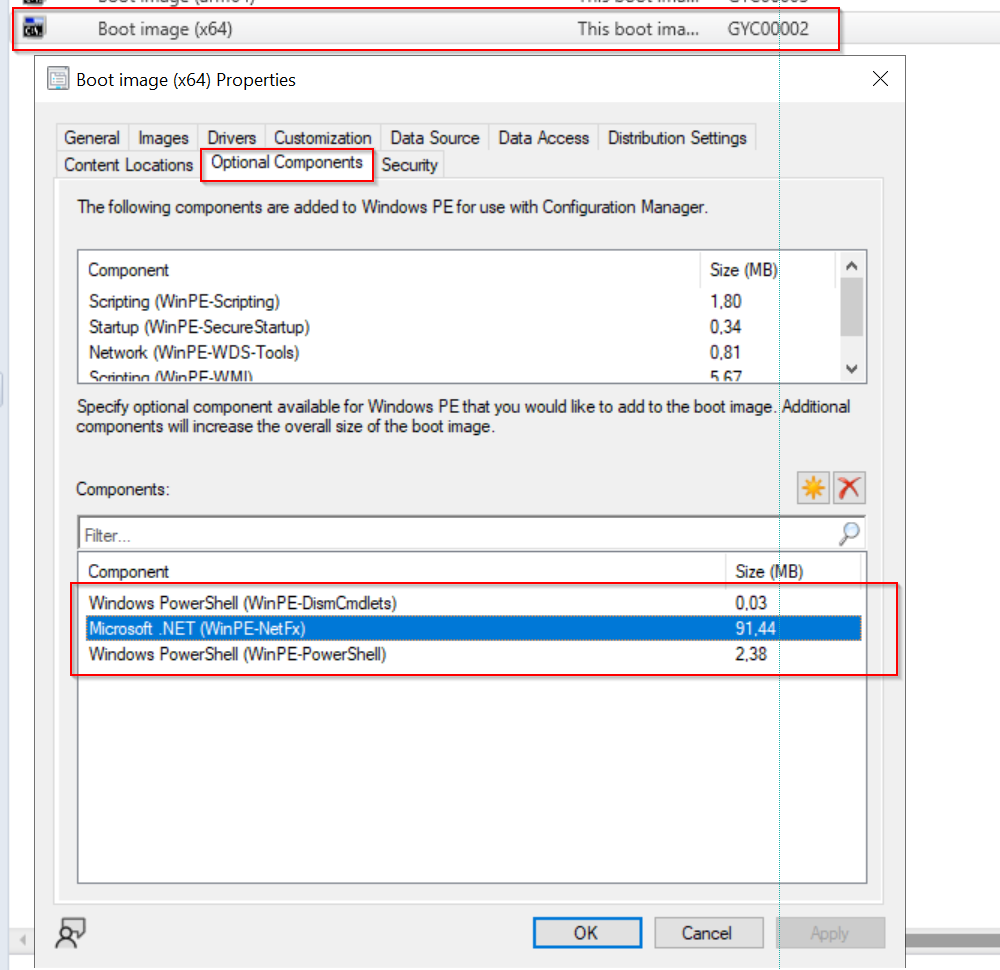
Before we begin, ensure that the following components are added to your boot image:
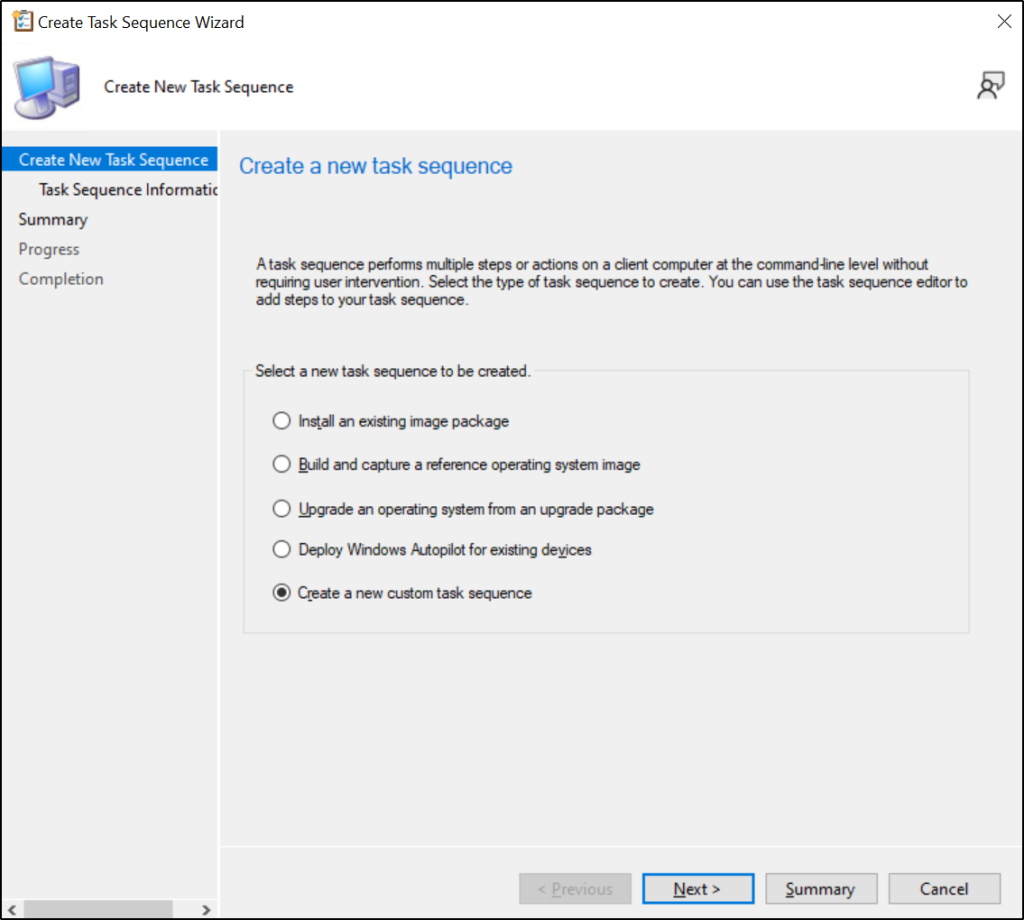
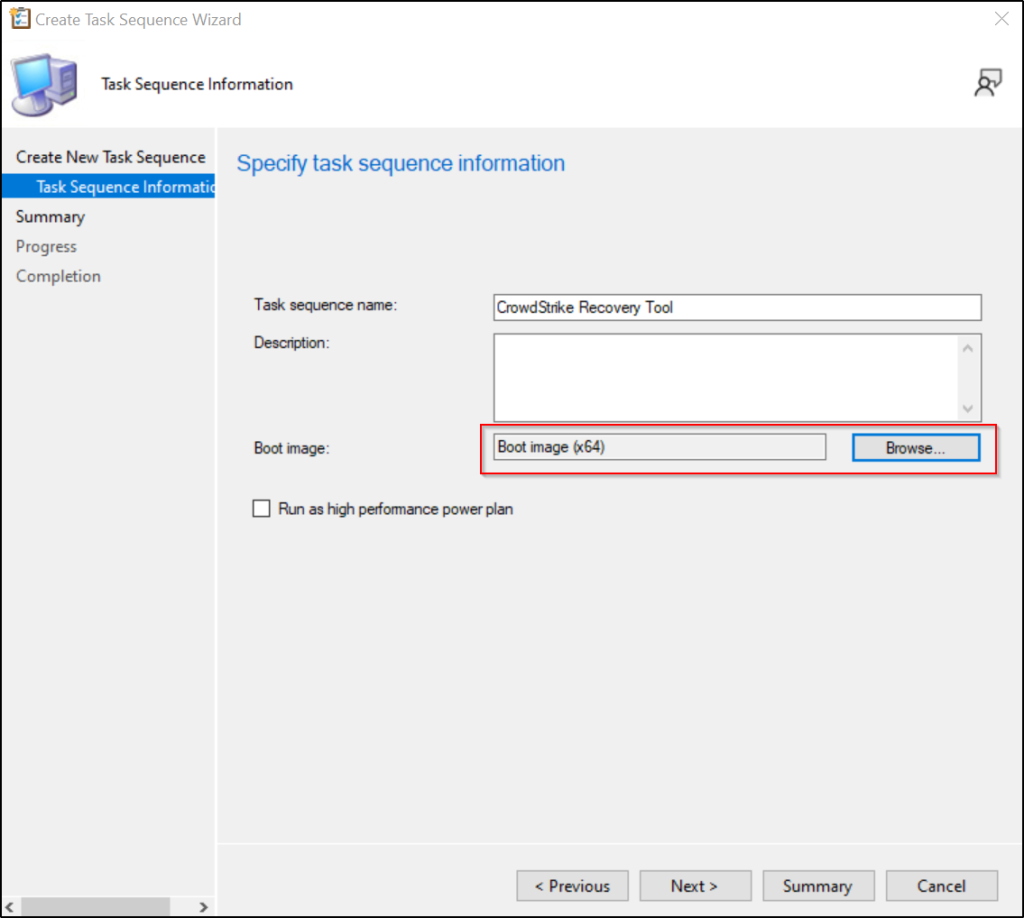
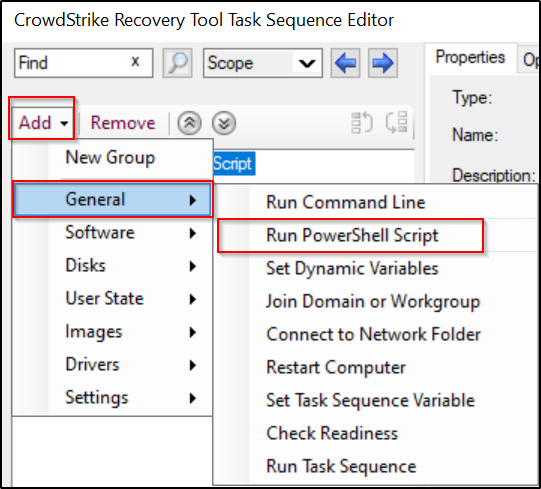
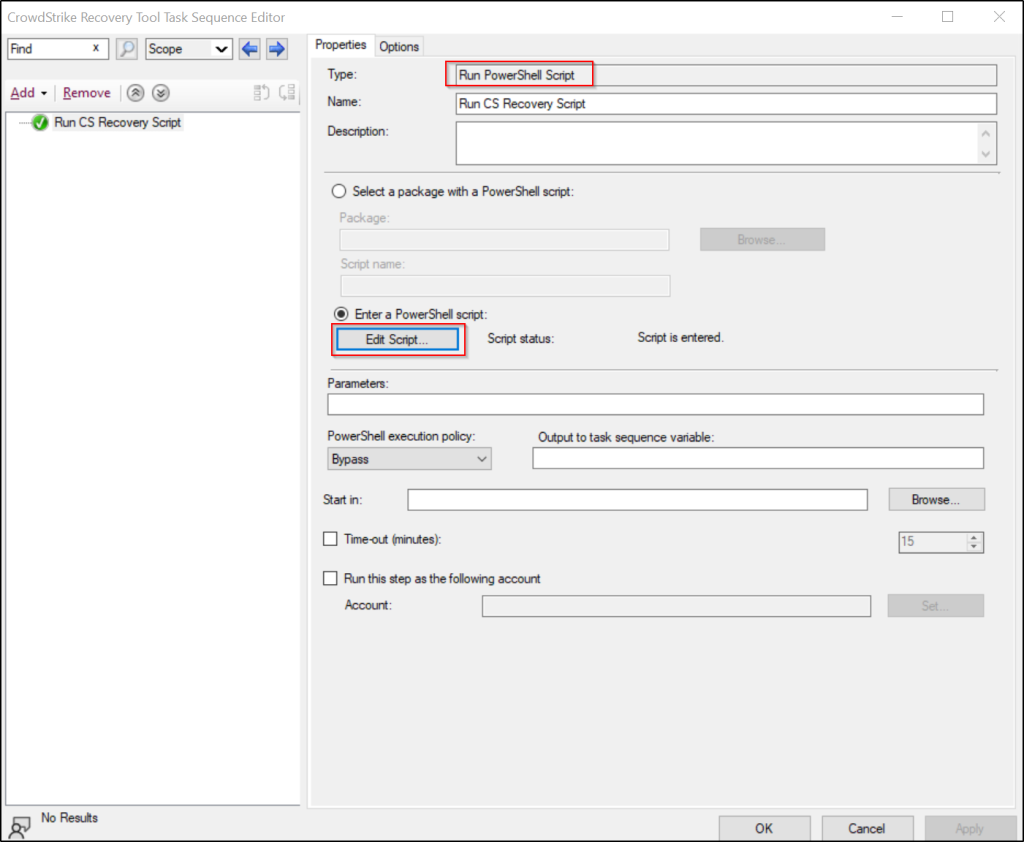
After downloading the tool, we can create a task sequence.
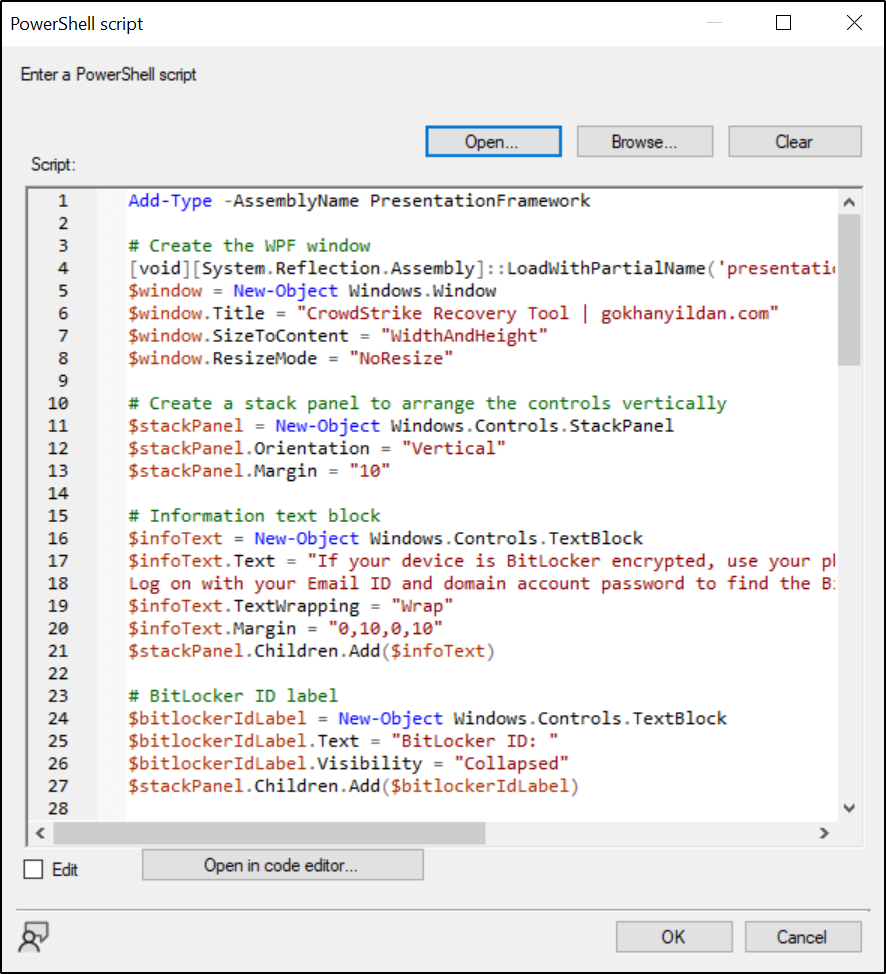
Paste the script into the window, then click OK.
Step 3: Deploy the Tool
To deploy this tool, you can select a collection that includes the problematic machines, or you can deploy it to all devices, as it will need to be manually selected since we are deploying it as an available application.
Since we will be running it from PXE, choose the “Only media and PXE” option with the Available deployment purpose.
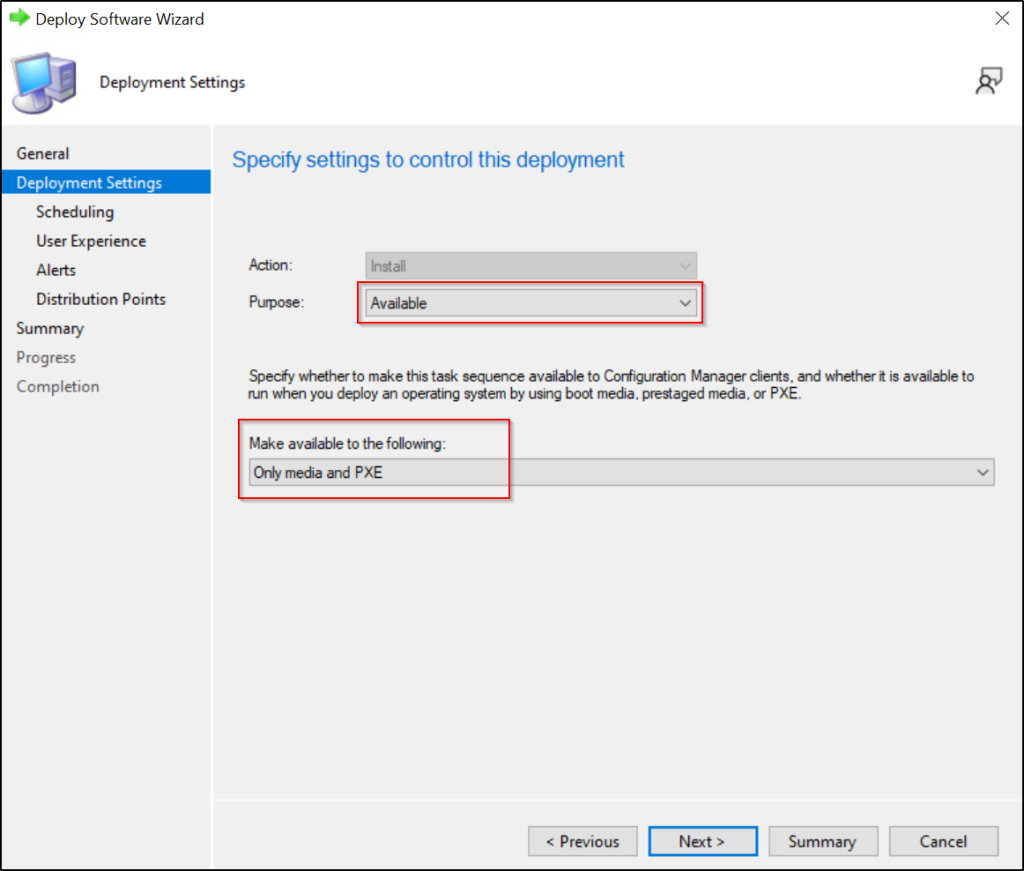
You can now finalize the process.
Step 4: Using Tool
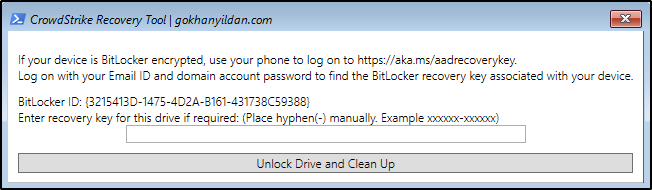
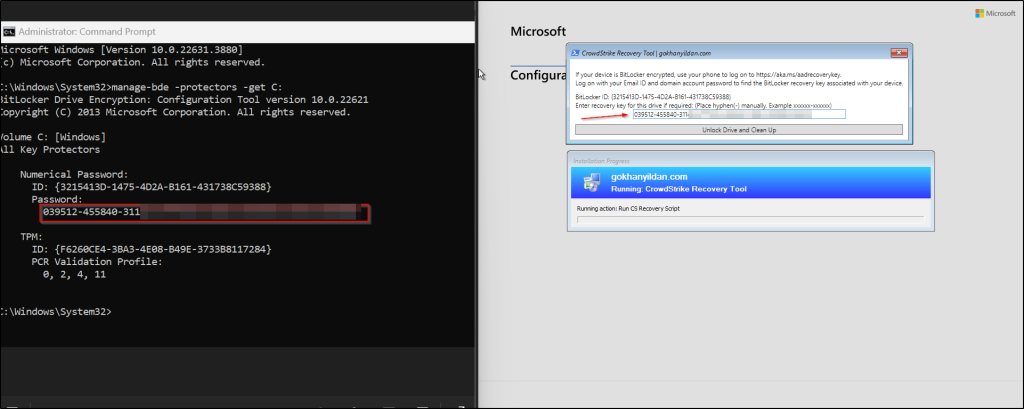
With Bitlocker Encryption:
Since I don’t have any problematic devices, I created the file that will need to be deleted manually.
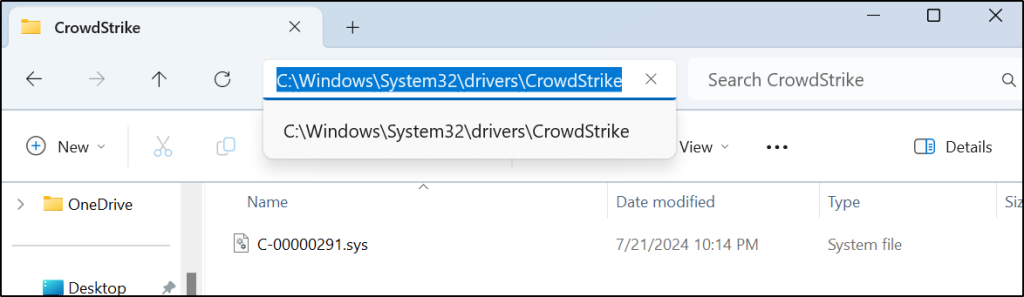
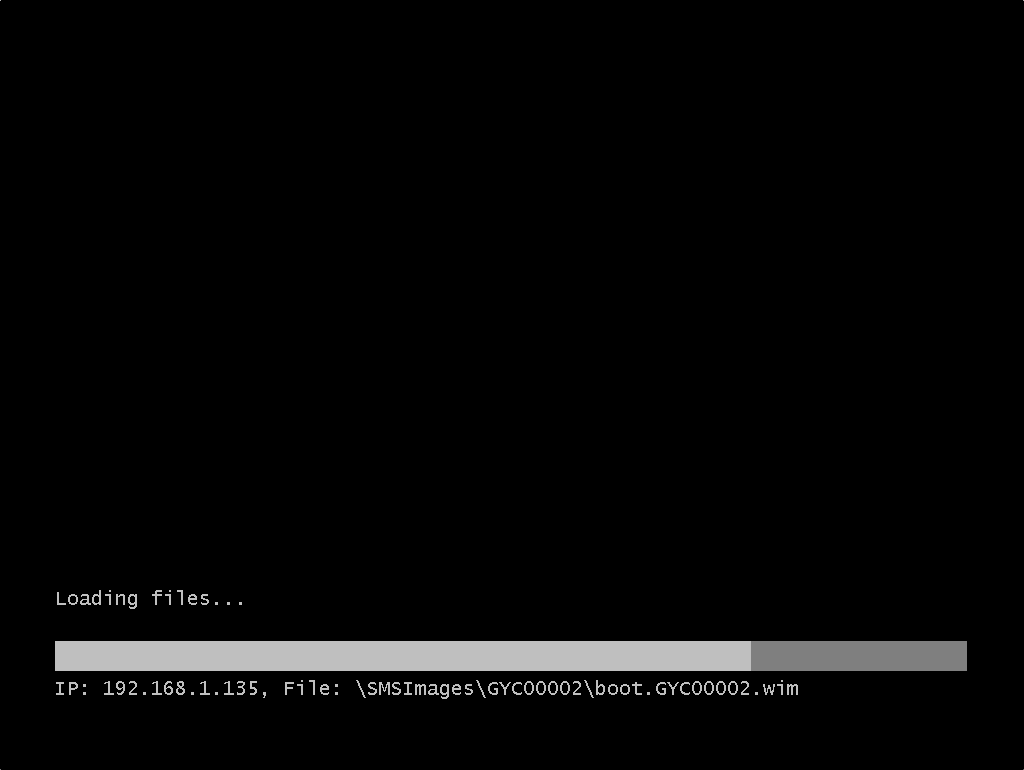
Boot the problematic device using SCCM PXE.
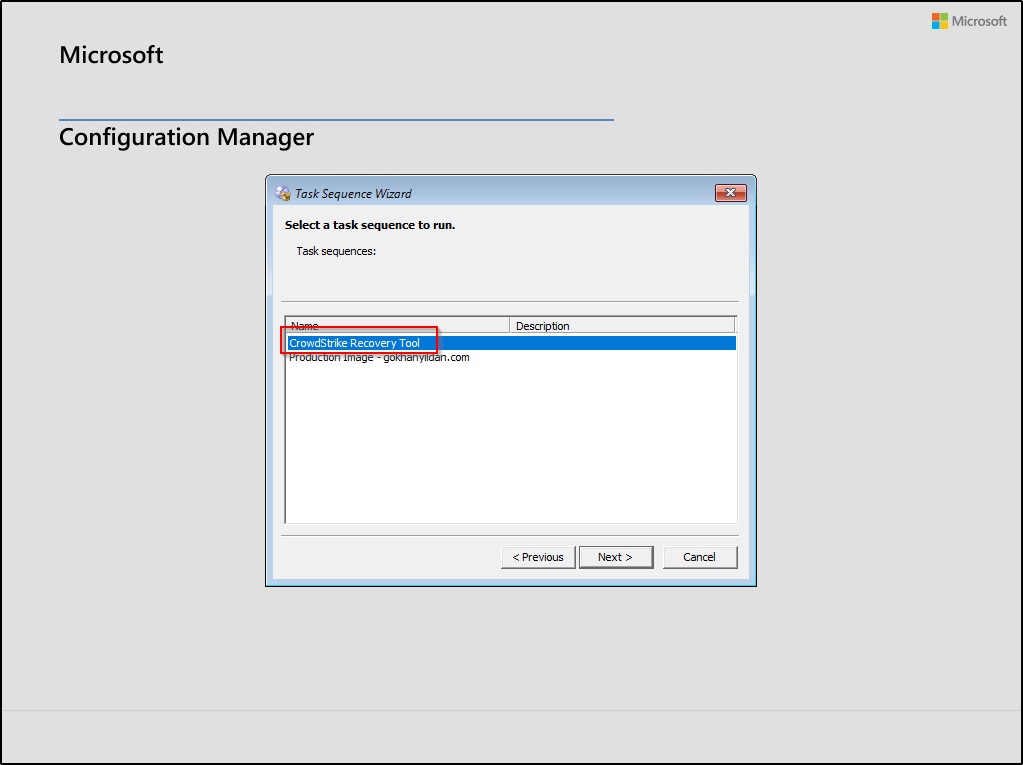
You will then see our task sequence.
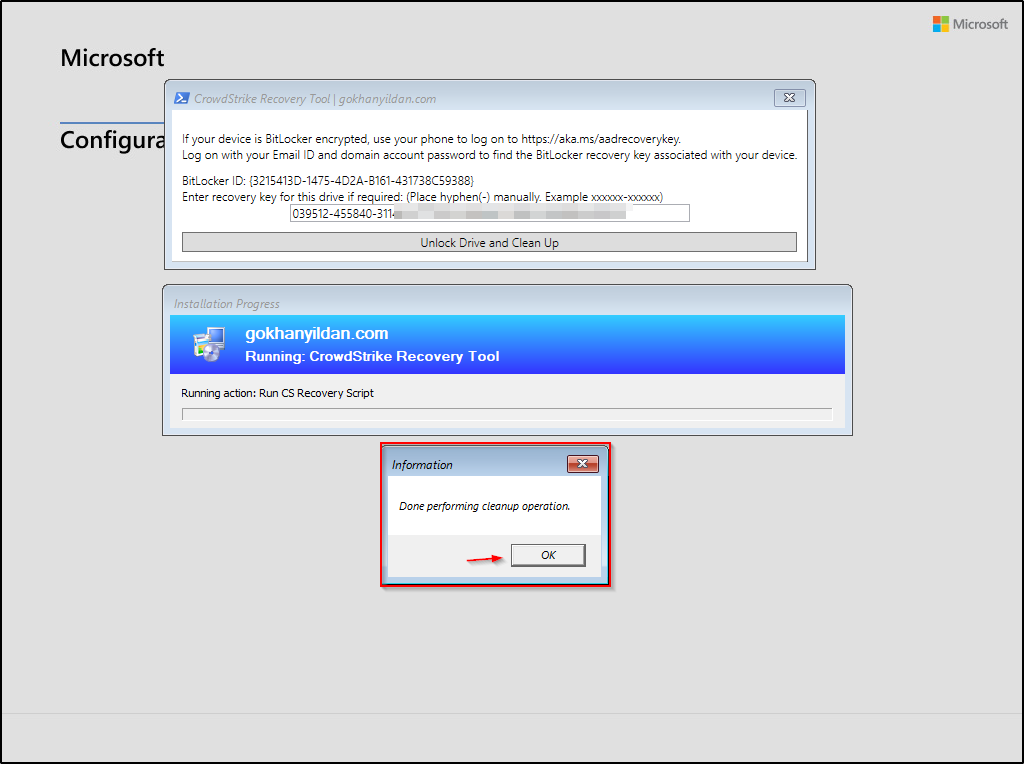
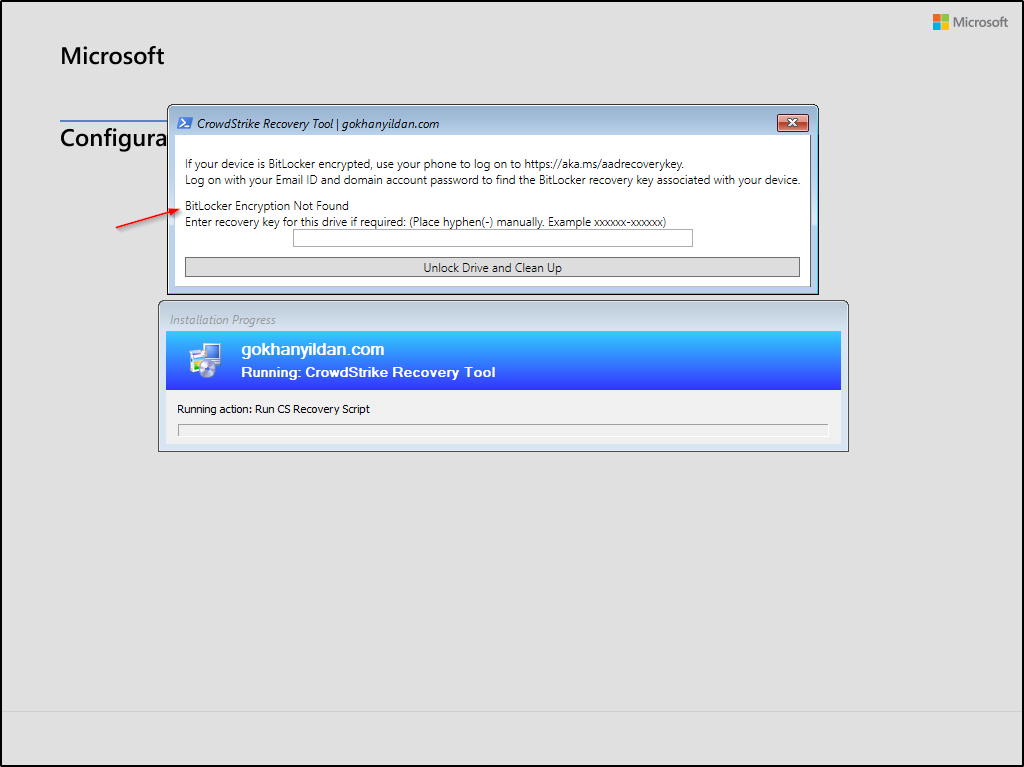
After selecting “CrowdStrike Recovery Tool,” a window will appear. If the device drive is encrypted, it will display the “BitLocker ID.” Enter the recovery key associated with that ID.
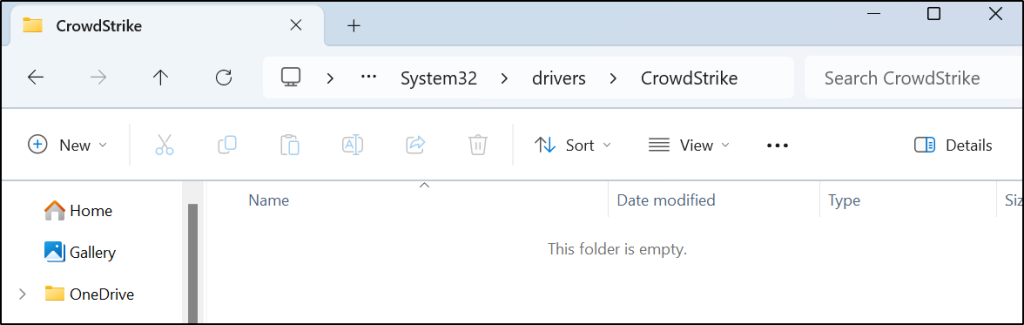
As you can see, the problematic file has been deleted.
Without Bitlocker Encryption:
This time it says “Bitlocker Encryption Not Found” and you can directly run the tool.
Thanks.
References: